The Goal: Reduce the risk of potential business productivity loss resulting from the retirement and consolidation of multiple file servers.
The Situation: A major corporation was migrating to a new centralized Microsoft Windows Server file server system, but had tens of millions of files still residing on its old file servers, which were scheduled to be retired. Any one of these critical business files could be mission-critical to some employee at the company, due to data in these files being linked to from one of these applications:
- MS Access
- MS Excel
- MS Word
- MS PowerPoint
- Rich-Text Files
- Adobe Acrobat
- Unstructured data such as video
But there was no easy way to identify the critical files. A “bottom up” approach of asking employees which files they linked to was not considered sufficiently reliable. A purely manual approach, examining each relevant file by hand, would have taken 100 to 1000 times more effort than was available to complete the migration.
Buy vs. Build: No commercial solution was available to adequately solve the problem.
Therefore, an automated tool had to be built that would identify the critical server dependent files without employee intervention. The tool to be developed had to perform this delicate operation systematically, reliably (to be able to be stopped and started from a point in time), contain built-in progress reporting and provide accountability and a full audit trail.
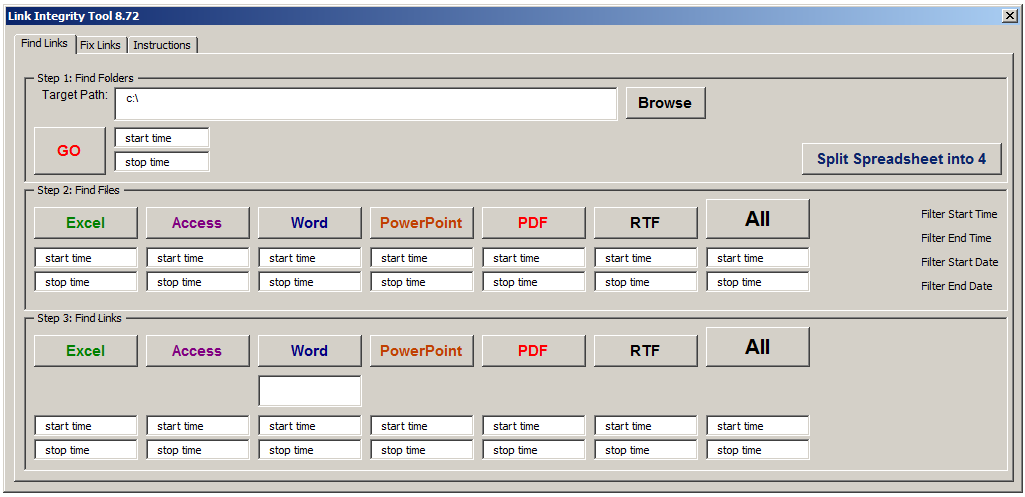
The solution was designed and developed on the Microsoft Excel platform, with a user-friendly dashboard as the intuitive and interactive interface to the tool. The tool was able to scan huge file servers and inspect the contents of all relevant files to see if they had links to the servers destined for retirement.
Actions – Solution Evolution: The tool was developed and refined over a period of six months, with continual feedback from the client’s experiences encountered during operating the tool. When suspect files where located, the users with the suspect files were notified and given a report which identified which of their critical files needed attention to be resolved.
The tool, throughout it’s continued development and refinement, evolved to contain additional sophisticated features.
For example, the tool was able to successfully navigate a complex file structure despite being “knocked off” the structure every time a corrupt file was located. The tool was enhanced to be split into two individual components, one of which was able to sense that the other had failed and then take corrective action by restarting the tool at the correct point in the processing. This enhancement make the tool very reliable and ability to be ran continuously twenty four hours a day without human intervention nor incurring costly human man-hours.
The tool was also able to be multiplexed – to run multiple instances of itself simultaneously on one PC, and able to “spawn” new instances of itself without interrupting a parent instance already running over the network. The tool could be pointed at the same target server from multiple PCs and have multiple instances all running at the same time. This divide and conquer approach utilized generic PC hardware, enabled rapid progress, and allowed for the most critical servers to get preference and be retired ahead of schedule.
Results: The tool is able to understand and detect a wide variety of file links, ranging from attached MS Access tables to links only present in modules of VBA code. It is able to cope with a score of anomalies frequently present in the target files and poorly documented by Microsoft, if documented at all.
The tool is self-documenting in operation and generates a record of its operation that dovetails well with the need to manage and validate its use. The tool automatically generates Excel output reports which facilitate distribution and resolution by client employee name and by server.
This tool has been seasoned and hardened with months of testing and performance tuning resulting in a finished product which performs 10x faster than the original design.
The user interface is intuitive and easy enough to use by non-technical people or clerical staff.
The business value and safeguarding of potential loss of business productivity resulting from a failure to recognize critical dependencies between files before retiring a server cannot be over stated.
“The insurance and confidence this tool provides to the technical staff when preparing to retire a server is tremendous and cannot be over stated.”
The tool’s graphical user interface (GUI) appears below: