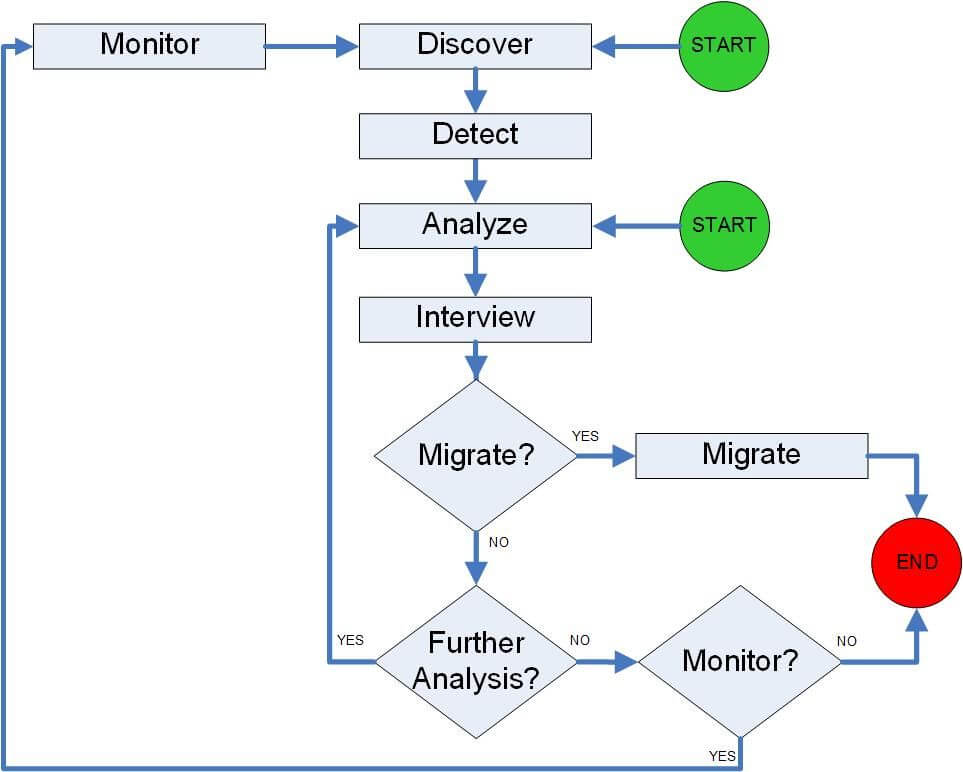
Conceptual View – Diagram
This strategy is to perform a series of discoveries and verifications with greater and greater depth of analysis on the fewest (the risky) suspect MS Access database applications. The approach reduces the overall time and ensures business users are given the necessary facts in order to make intelligent support decisions.
As we work on the suspect files, we funnel them down (filter out some) and increase the degree of magnification (deepen our analysis).